Inside the Lighthouse and Lucid PhaaS Campaigns Targeting 316 Global Brands
Key Data
Netcraft has identified two phishing campaigns believed to be associated with the Lighthouse and Lucid Phishing-as-a-Service (PhaaS) platforms. Since identifying these campaigns, we have detected more than 17,500 phishing domains powered by them targeting 316 brands from 74 countries.
We have identified a link between the Lucid and Lighthouse platforms through use of near-identical anti-monitoring pages.
We have also deployed targeted automation to enhance detection of Lucid PhaaS URLs.
Phishing-as-a-Service
Phishing-as-a-Service (PhaaS) deployments have risen significantly recently. The PhaaS operators charge a monthly fee for phishing software with pre-installed templates impersonating, in some cases, hundreds of brands from countries around the world.
Since we started tracking Darcula, another popular PhaaS, in 2023, we have seen a rise in similar kits also utilizing modern technologies and offering ease of use, allowing fraudsters to conduct phishing without having extensive technical knowledge.
June 2025 was our biggest month to date in terms of Phishing-as-a-Service detections: 13.5% of phishing hostnames that we detected were powered by one of the Phishing-as-a-Service platforms that we are tracking.

Figure 1. Phishing-as-a-Service hostnames detected by Netcraft by Month.
Lucid Phishing-as-a-Service
One high volume Phishing-as-a-Service that we have been tracking matches up with Prodraft’s fingerprinting of Lucid Phishing-as-a-Service.
The Lucid PhaaS platform allows setup of phishing campaigns targeting a wide range of industries including toll companies, governments, postal companies, and financial institutions.

Figure 2. Example Lucid Phishing-as-a-Service site impersonating finance company Kuda.
In Lucid, each phishing template is given a unique name, for example, the phishing site above impersonating Kuda is running the kuda295 theme.
Typically, Lucid phishing URLs are protected from being visited by people/organisations other than intended victims in the following ways:
· A specific path, e.g. /servicios is required to see the phishing content, these are fraudster-configured so they are hard to predict and can vary widely even across phishing pages targeting the same brand.
· A specific proxy country is required to see the phishing content.
· A mobile User-Agent is required to see the phishing content.
If not matching all the anti-monitoring criteria, a generic fake shop is shown rather than the actual phishing site.

Figure 3. Anti-monitoring content displaying a fake shoe shop.

Figure 4. Anti-monitoring content displaying a fake women's clothing shop.
We have detected phishing URLs targeting 164 brands based in 63 different countries hosted through the Lucid platform.

Figure 5. Number of Lucid hostnames per country of targeted brand.
Lighthouse Phishing-as-a-Service Kit
Lighthouse is a Phishing-as-a-Service kit by developer WangDuoYu. It receives frequent updates and allows fraudsters to steal 2FA credentials through customizable phishing templates.
Prices for Lighthouse PhaaS range from 88 USD for a weekly subscription, to 1588 USD for a yearly subscription.
We have attributed a phishing campaign that makes use of heavy HTML obfuscation to the Lighthouse kit through the following links:
This phishing campaign uses identical templates to those demonstrated in Lighthouse sales material.
We have detected this phishing campaign installed on the test-24[.]top domain used by WangDuoYu in demonstration videos.

Figure 6. Lighthouse phishing URL impersonating the Albanian postal service Posta Shqiptare.
Anti-monitoring for this campaign uses the same 'LOAFING OUT LOUD’ fake shop template as used by the Lucid Phishing-as-a-Service, though the HTML differs slightly between the two.

Figure 7. Lighthouse using the same anti-monitoring content as seen in Lucid URLs.

Figure 8. Screenshot of Lighthouse demo video, indicating use of test-24[.]top domain for testing.
One other subdomain of test-24[.]top that we detected is haozi[.]test-24[.]top, which is interesting as we have previously covered the Haozi group in our Haozi’s Plug-and-Play Phishing-as-a-Service Has Facilitated $280,000 of Criminal Transactions Over Past Five Months blog post. We have not detected any content installed on this haozi hostname.
Previously, when researching Haozi, we noticed that one of the Haozi Telegram group administrators was a member of the laowangLiveGroup telegram group where WangDuoYu is an administrator.
We have detected Lighthouse phishing URLs targeting 204 brands based in 50 different countries.
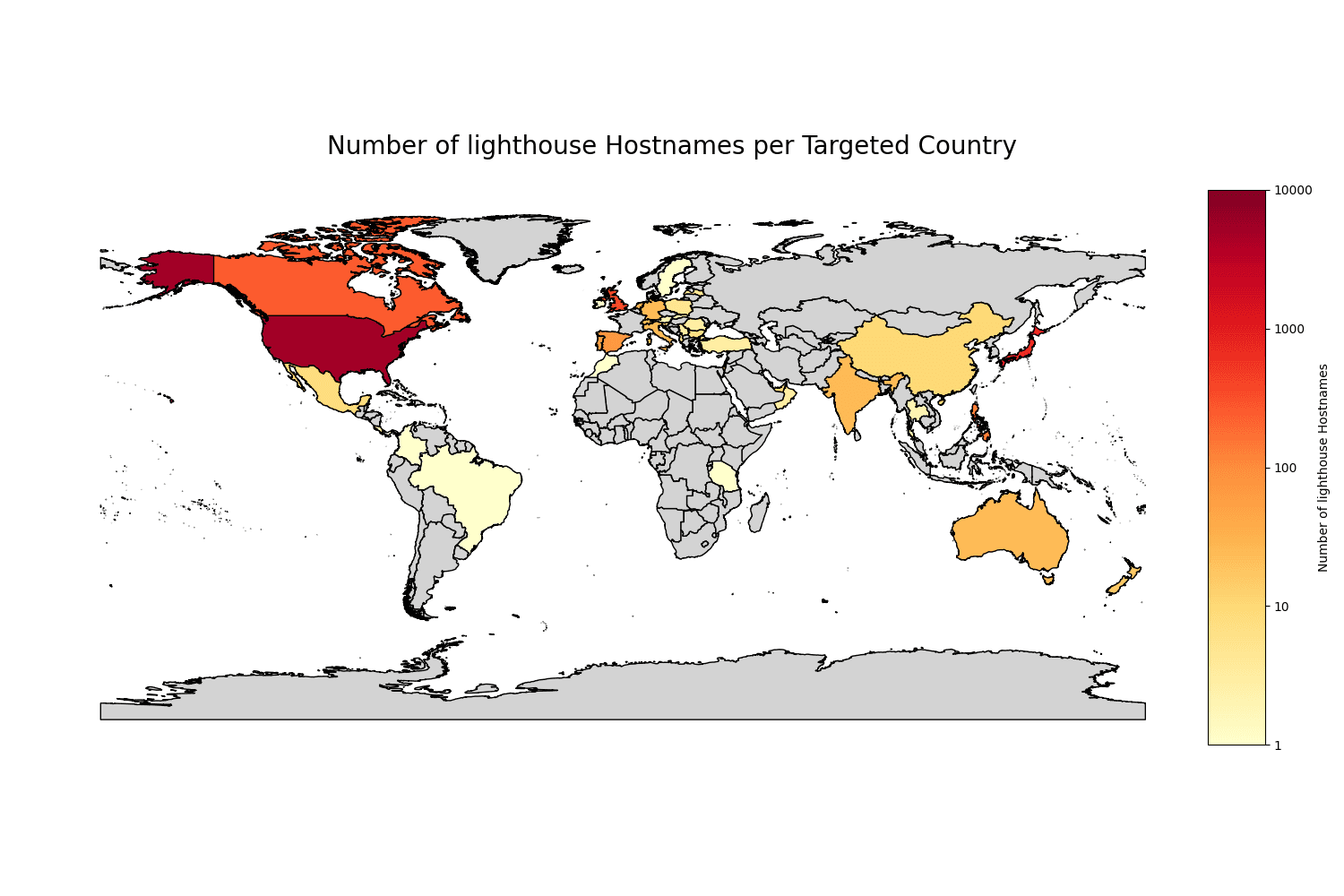
Figure 9. Number of lighthouse hostnames per country of targeted brand.
Conclusion
Phishing-as-a-Service is increasingly lowering the bar for cybercrime, enabling massive and highly sophisticated attacks against brands globally. Lucid and Lighthouse are examples of how fast the growth and evolution of these platforms can occur and how difficult they can sometimes be to disrupt.
Netcraft is contributing to the reduced impact of these operations through the correlation of campaigns, the discovery of common infrastructure, and the implementation of targeted automation. We will continue to monitor these tactics and share our findings as they develop.
As PhaaS kits become ever more sophisticated and complex, proactive intelligence and rapid disruption will remain important to protect users and brands across the internet.
Join our mailing list for regular blog posts and case studies from Netcraft.





