





Solutions for Media and Entertainment
You’ve Built a Brand, Protect It
Scale your brand protection efforts across your brand portfolio and executives across all channels.
The Netcraft Difference
Media and entertainment is big business — and an attractive target for criminals to steal accounts and resell that data. Netcraft’s advanced automation disrupts credential sales across the internet — including the clear, deep, and dark web — and takes down the sites or listings to protect you and your customers.
High Profile Means High Risk

Identification Across Online Ecosystems
Prevent attacks that have become increasingly sophisticated and span evolving platforms.

Unprecedented Scale and New Threats
Keep your team focused on what matters most while Netcraft automatically detects threats across 100+ domains.

Increasing Complexity and Cloaking
Gain a more complete view of your threat landscape, your brands, and how attackers impersonate you online.

Identification Across Online Ecosystems
Prevent attacks that have become increasingly sophisticated and span evolving platforms.

Identification Across Online Ecosystems
Prevent attacks that have become increasingly sophisticated and span evolving platforms.

Unprecedented Scale and New Threats
Keep your team focused on what matters most while Netcraft automatically detects threats across 100+ domains.

Increasing Complexity and Cloaking
Gain a more complete view of your threat landscape, your brands, and how attackers impersonate you online.

Identification Across Online Ecosystems
Prevent attacks that have become increasingly sophisticated and span evolving platforms.
Protect Your Business and Customers
from stolen accounts
Brand Impersonation
Brand Impersonation
Brand Impersonation
Brand Impersonation
Ads
Ads
Ads
Ads
Deep & Dark Web
Deep & Dark Web
Deep & Dark Web
Deep & Dark Web
Scams
Scams
Scams
Scams
Social Media Impersonation
Social Media Impersonation
Social Media Impersonation
Social Media Impersonation
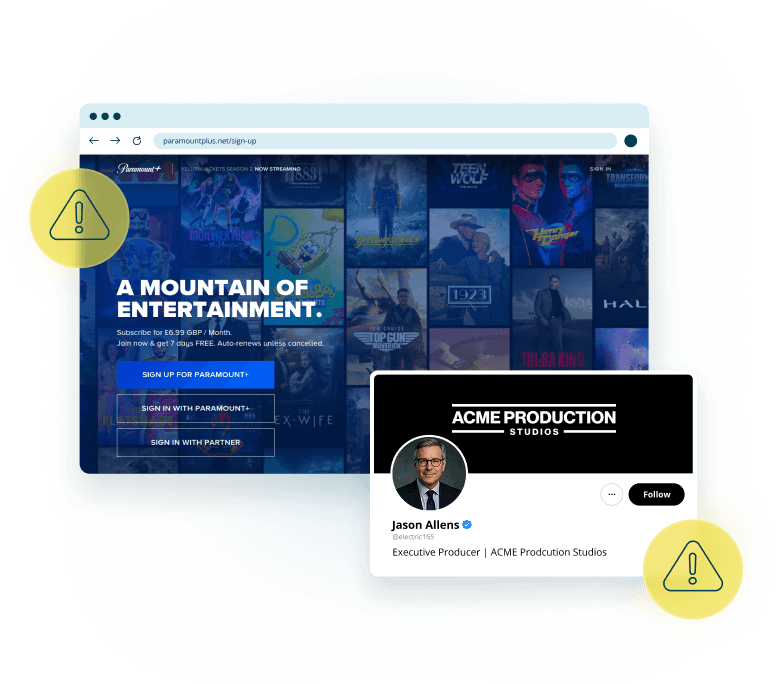



Built for Media and Entertainment Companies
Advanced Threat Detection
Advanced Threat Detection
Advanced Threat Detection
Advanced Threat Detection
Through abuse box processing, clients can have all screenshots of scams sent directly to Netcraft. Using OCR, Netcraft auto-extracts phone numbers, URLs, and other information to submit to our threat feeds and ensure scam disruption.








Attack Visibility and Analysis
Attack Visibility and Analysis
Attack Visibility and Analysis
Attack Visibility and Analysis
Safely explore an attack site without spinning up virtual machines, grab any evidence you need, and automatically have that evidence reported to your takedown tool to be disrupted.
Tell a Good News Story
Tell a Good News Story
Tell a Good News Story
Tell a Good News Story
With customized dashboards and real-time reporting, view your security footprint in one view, easily showing the impact your team is having on protecting the organization.




Unmatched Scale and Effectiveness
Netcraft’s online brand protection operates 24/7 to discover and stop phishing, fraud, scams, and cyber attacks through extensive automation, AI, machine learning, and human insight.



1.9 hr
1.9 hr
1.9 hr
1.9 hr
phishing median takedown time
phishing median takedown time



10M+
10M+
10M+
10M+
threat reports and suspicious URLs analyzed every day
threat reports and suspicious URLs analyzed every day



25M+
25M+
25M+
25M+
attacks taken down and growing
attacks taken down and growing
Trusted Compliance and Security










Frequently Asked Questions
What is a phishing attack?
A phishing attack is when a cybercriminal uses scam emails, websites, or text messages to trick victims. The aim is often to steal money or acquire sensitive information (such as credentials).
How do cybercriminals use phishing attacks?
Cybercriminals create emails and websites that convincingly impersonate legitimate brands to trick victims into providing their credentials (login details). These credentials can then be sold online by cybercriminals.
How else might criminals acquire credentials?
Criminals can use malicious JavaScript embedded into compromised web pages to automatically send sensitive details (such as credentials and payment details) to an account they control.
How does Netcraft defend against these types of attacks?
Netcraft automatically identifies hosting providers, domain registrars, webmasters, and others — and determines how to notify them most effectively (via email, API, private contact, or otherwise). We gather and present evidence of the cyberattack to demonstrate the problem to those with the ability to take down the attack. Netcraft is also able to take down email addresses found in phishing kits that have been identified as receiving the stolen credentials.
How quickly can fake websites impersonating my brand be taken down?
A suspected scam website can be analyzed, validated, and takedown notifications dispatched within minutes of discovery. Content can be taken down within hours if the company that is hosting the fraudulent content is reputable.
What is a phishing attack?
A phishing attack is when a cybercriminal uses scam emails, websites, or text messages to trick victims. The aim is often to steal money or acquire sensitive information (such as credentials).
How do cybercriminals use phishing attacks?
Cybercriminals create emails and websites that convincingly impersonate legitimate brands to trick victims into providing their credentials (login details). These credentials can then be sold online by cybercriminals.
How else might criminals acquire credentials?
Criminals can use malicious JavaScript embedded into compromised web pages to automatically send sensitive details (such as credentials and payment details) to an account they control.
How does Netcraft defend against these types of attacks?
Netcraft automatically identifies hosting providers, domain registrars, webmasters, and others — and determines how to notify them most effectively (via email, API, private contact, or otherwise). We gather and present evidence of the cyberattack to demonstrate the problem to those with the ability to take down the attack. Netcraft is also able to take down email addresses found in phishing kits that have been identified as receiving the stolen credentials.
How quickly can fake websites impersonating my brand be taken down?
A suspected scam website can be analyzed, validated, and takedown notifications dispatched within minutes of discovery. Content can be taken down within hours if the company that is hosting the fraudulent content is reputable.
What is a phishing attack?
A phishing attack is when a cybercriminal uses scam emails, websites, or text messages to trick victims. The aim is often to steal money or acquire sensitive information (such as credentials).
How do cybercriminals use phishing attacks?
Cybercriminals create emails and websites that convincingly impersonate legitimate brands to trick victims into providing their credentials (login details). These credentials can then be sold online by cybercriminals.
How else might criminals acquire credentials?
Criminals can use malicious JavaScript embedded into compromised web pages to automatically send sensitive details (such as credentials and payment details) to an account they control.
How does Netcraft defend against these types of attacks?
Netcraft automatically identifies hosting providers, domain registrars, webmasters, and others — and determines how to notify them most effectively (via email, API, private contact, or otherwise). We gather and present evidence of the cyberattack to demonstrate the problem to those with the ability to take down the attack. Netcraft is also able to take down email addresses found in phishing kits that have been identified as receiving the stolen credentials.
How quickly can fake websites impersonating my brand be taken down?
A suspected scam website can be analyzed, validated, and takedown notifications dispatched within minutes of discovery. Content can be taken down within hours if the company that is hosting the fraudulent content is reputable.
What is a phishing attack?
A phishing attack is when a cybercriminal uses scam emails, websites, or text messages to trick victims. The aim is often to steal money or acquire sensitive information (such as credentials).
How do cybercriminals use phishing attacks?
Cybercriminals create emails and websites that convincingly impersonate legitimate brands to trick victims into providing their credentials (login details). These credentials can then be sold online by cybercriminals.
How else might criminals acquire credentials?
Criminals can use malicious JavaScript embedded into compromised web pages to automatically send sensitive details (such as credentials and payment details) to an account they control.
How does Netcraft defend against these types of attacks?
Netcraft automatically identifies hosting providers, domain registrars, webmasters, and others — and determines how to notify them most effectively (via email, API, private contact, or otherwise). We gather and present evidence of the cyberattack to demonstrate the problem to those with the ability to take down the attack. Netcraft is also able to take down email addresses found in phishing kits that have been identified as receiving the stolen credentials.
How quickly can fake websites impersonating my brand be taken down?
A suspected scam website can be analyzed, validated, and takedown notifications dispatched within minutes of discovery. Content can be taken down within hours if the company that is hosting the fraudulent content is reputable.
Resources & Insights
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.




