





Visibility That Drives Action
Threat Intelligence
Leverage validated, actionable threat intelligence to protect your business at any scale.
Data-Driven, Actionable Intelligence

Boost the Signal
Access verified and actionable cyber threat intelligence collected from expert curated sources — without the noise.
Stop More Threats
Identify threats across 100+ attack types, including phishing, malware, evil JavaScript, and peer-to-peer messaging scams.

Protect Your Brand 24/7
Leverage Netcraft’s extensive automation combined with human insight to validate threats around the clock.

Proactively Defend Against Attacks
Gain automated in-depth threat analysis for proactive defense against phishing kits, web shells, credential stuffing, and more.


Boost the Signal
Access verified and actionable cyber threat intelligence collected from expert curated sources — without the noise.

Boost the Signal
Access verified and actionable cyber threat intelligence collected from expert curated sources — without the noise.

Boost the Signal
Access verified and actionable cyber threat intelligence collected from expert curated sources — without the noise.
Stop More Threats
Identify threats across 100+ attack types, including phishing, malware, evil JavaScript, and peer-to-peer messaging scams.

Protect Your Brand 24/7
Leverage Netcraft’s extensive automation combined with human insight to validate threats around the clock.

Proactively Defend Against Attacks
Gain automated in-depth threat analysis for proactive defense against phishing kits, web shells, credential stuffing, and more.

Netcraft Threat Intelligence Capabilities
Our global threat feeds cover more than 100 threat types, including phishing, malware, and scams targeting any brand or institution, for clients and non-clients alike. These feeds are licensed broadly by the most popular web browsers and antivirus companies. Each day Netcraft protects billions of people against cyber attacks, often within minutes of detection.




Threat Feeds
Threat Feeds
Threat Feeds
Threat Feeds
Deploy an automatic array of countermeasures upon threat detection across multiple platforms and monitor to block threats in near real-time.
Scam Intelligence
Scam Intelligence
Scam Intelligence
Scam Intelligence
Let Netcraft intentionally be the first victim. Our peer-to-peer scam intelligence proactively detects and intercepts scams through encrypted conversations before they can harm your customers.




Step 1
INFORMATION GATHERING
Netcraft’s proprietary sources provide a global view of cybercrime activity. Combined with the network effect of reported abuse across the largest governments and providers in the world and a substantial anti-cybercrime reporting community, Netcraft ingests 23B+ proprietary datapoints annually.
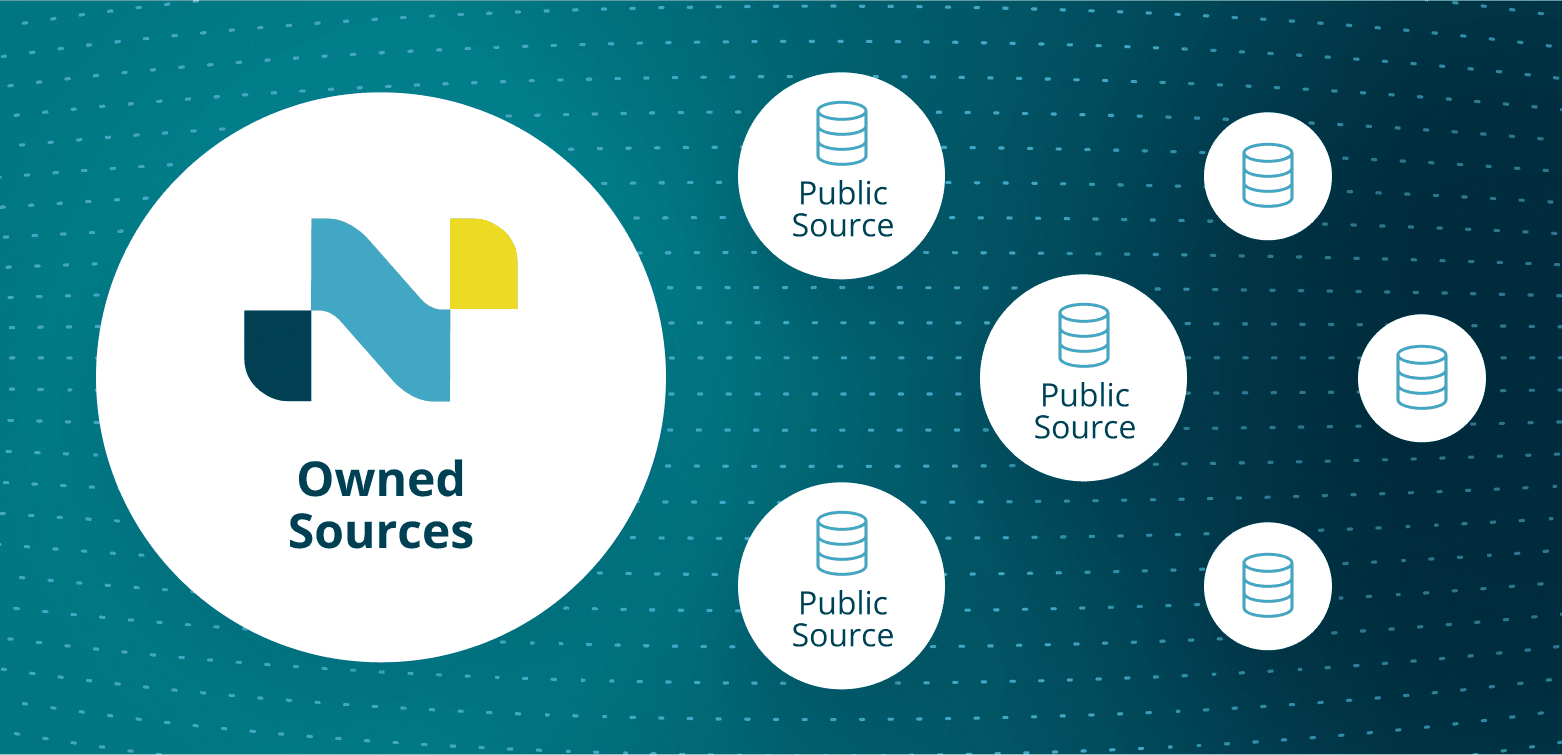
Step 1
INFORMATION GATHERING
Netcraft’s proprietary sources provide a global view of cybercrime activity. Combined with the network effect of reported abuse across the largest governments and providers in the world and a substantial anti-cybercrime reporting community, Netcraft ingests 23B+ proprietary datapoints annually.

Step 1
INFORMATION GATHERING
Netcraft’s proprietary sources provide a global view of cybercrime activity. Combined with the network effect of reported abuse across the largest governments and providers in the world and a substantial anti-cybercrime reporting community, Netcraft ingests 23B+ proprietary datapoints annually.

Step 1
INFORMATION GATHERING
Netcraft’s proprietary sources provide a global view of cybercrime activity. Combined with the network effect of reported abuse across the largest governments and providers in the world and a substantial anti-cybercrime reporting community, Netcraft ingests 23B+ proprietary datapoints annually.

Step 2
DISCOVERY TECHNIQUES
Criminals use devices and geo-blocking to circumvent IP-blocking techniques. We fetch content from our network of 250+ proxies to bypass blocking techniques.
Additional discovery techniques include:
Headless browser to enable safe, accurate attack analysis
Screenshot Tool to capture attacks across devices and countries
Multi-stage attack exploration with automated form filling to expedite analysis

Step 2
DISCOVERY TECHNIQUES
Criminals use devices and geo-blocking to circumvent IP-blocking techniques. We fetch content from our network of 250+ proxies to bypass blocking techniques.
Additional discovery techniques include:
Headless browser to enable safe, accurate attack analysis
Screenshot Tool to capture attacks across devices and countries
Multi-stage attack exploration with automated form filling to expedite analysis

Step 2
DISCOVERY TECHNIQUES
Criminals use devices and geo-blocking to circumvent IP-blocking techniques. We fetch content from our network of 250+ proxies to bypass blocking techniques.
Additional discovery techniques include:
Headless browser to enable safe, accurate attack analysis
Screenshot Tool to capture attacks across devices and countries
Multi-stage attack exploration with automated form filling to expedite analysis

Step 2
DISCOVERY TECHNIQUES
Criminals use devices and geo-blocking to circumvent IP-blocking techniques. We fetch content from our network of 250+ proxies to bypass blocking techniques.
Additional discovery techniques include:
Headless browser to enable safe, accurate attack analysis
Screenshot Tool to capture attacks across devices and countries
Multi-stage attack exploration with automated form filling to expedite analysis

Step 3
THREAT CLASSIFICATION
Our sophisticated automated classification system confirms an attack type and attributes it to an impersonated entity across a wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis leverages AI and machine learning models, automating and operating without interruption 24/7. Manual intervention is limited to edge cases, high-risk blocks, and to improve future automated classification.

Step 3
THREAT CLASSIFICATION
Our sophisticated automated classification system confirms an attack type and attributes it to an impersonated entity across a wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis leverages AI and machine learning models, automating and operating without interruption 24/7. Manual intervention is limited to edge cases, high-risk blocks, and to improve future automated classification.

Step 3
THREAT CLASSIFICATION
Our sophisticated automated classification system confirms an attack type and attributes it to an impersonated entity across a wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis leverages AI and machine learning models, automating and operating without interruption 24/7. Manual intervention is limited to edge cases, high-risk blocks, and to improve future automated classification.

Step 3
THREAT CLASSIFICATION
Our sophisticated automated classification system confirms an attack type and attributes it to an impersonated entity across a wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis leverages AI and machine learning models, automating and operating without interruption 24/7. Manual intervention is limited to edge cases, high-risk blocks, and to improve future automated classification.

Step 4
FRAUDCASTING
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are licensed broadly by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is underway.

Step 4
FRAUDCASTING
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are licensed broadly by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is underway.

Step 4
FRAUDCASTING
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are licensed broadly by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is underway.

Step 4
FRAUDCASTING
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are licensed broadly by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is underway.

Disruption at Any Scale
Netcraft’s digital risk protection platform covers 100+ cyber attack types including phishing, malware, investment scams, advance fee fraud, and much more. Some of the following are the most prominent threats experienced by clients.
Phishing
Netcraft takes down around one-third of the world’s phishing attacks, operating with careful automation on a global scale, establishing us as the most trusted takedown provider in the world.
Conversational Scams
Netcraft uses AI to engage directly with scammers, allowing us to detect and interact with received scams targeting your company to reveal the anatomy of the scam, exposing any financial details, and take down attack infrastructure.
Smishing and Vishing
Detecting and disrupting smishing and vishing threats requires a multi-threaded detection and disruption methodology. Netcraft can detect and take down malicious phone numbers, as well as any links to additional attacker-controlled infrastructure used to support the attack.
Survey and Support Scams
Survey scams trick victims into thinking they’ll get a valuable reward, often using well-known brand names and fake gift card offers. Technical support scams involve fake agents — usually via calls or pop-ups — claiming there’s a problem with your device to steal personal info or charge for bogus help.
Malware
Instead of stealing information directly, this attack lures users to a site that secretly installs malicious code on their device. It can involve infected files, malicious documents, harmful JavaScript, or shopping site skimmers. Netcraft helps stop these threats by detecting and blocking malicious websites.
Ransomware
Respond to the first signs of a cyber attack by taking down the machines targeting your organization, whether they’re part of custom-built attack infrastructure or compromised devices in botnet attacks. Many organizations use SIEM tools to detect failed logins, blocked exploits, and mitigate denial of service attacks. Netcraft automatically uses this data to counter cybercriminals in real time, eliminating the need for manual intervention.
Web Shells
Malicious scripts known as web shells are implanted on compromised servers to give attackers remote control and unauthorized access. They serve as persistent backdoors for executing commands and manipulating the server. Netcraft identifies, blocks, and removes these web shells, cutting off attackers from restarting or escalating their campaigns.
Phishing
Netcraft takes down around one-third of the world’s phishing attacks, operating with careful automation on a global scale, establishing us as the most trusted takedown provider in the world.
Conversational Scams
Netcraft uses AI to engage directly with scammers, allowing us to detect and interact with received scams targeting your company to reveal the anatomy of the scam, exposing any financial details, and take down attack infrastructure.
Smishing and Vishing
Detecting and disrupting smishing and vishing threats requires a multi-threaded detection and disruption methodology. Netcraft can detect and take down malicious phone numbers, as well as any links to additional attacker-controlled infrastructure used to support the attack.
Survey and Support Scams
Survey scams trick victims into thinking they’ll get a valuable reward, often using well-known brand names and fake gift card offers. Technical support scams involve fake agents — usually via calls or pop-ups — claiming there’s a problem with your device to steal personal info or charge for bogus help.
Malware
Instead of stealing information directly, this attack lures users to a site that secretly installs malicious code on their device. It can involve infected files, malicious documents, harmful JavaScript, or shopping site skimmers. Netcraft helps stop these threats by detecting and blocking malicious websites.
Ransomware
Respond to the first signs of a cyber attack by taking down the machines targeting your organization, whether they’re part of custom-built attack infrastructure or compromised devices in botnet attacks. Many organizations use SIEM tools to detect failed logins, blocked exploits, and mitigate denial of service attacks. Netcraft automatically uses this data to counter cybercriminals in real time, eliminating the need for manual intervention.
Web Shells
Malicious scripts known as web shells are implanted on compromised servers to give attackers remote control and unauthorized access. They serve as persistent backdoors for executing commands and manipulating the server. Netcraft identifies, blocks, and removes these web shells, cutting off attackers from restarting or escalating their campaigns.
Phishing
Netcraft takes down around one-third of the world’s phishing attacks, operating with careful automation on a global scale, establishing us as the most trusted takedown provider in the world.
Conversational Scams
Netcraft uses AI to engage directly with scammers, allowing us to detect and interact with received scams targeting your company to reveal the anatomy of the scam, exposing any financial details, and take down attack infrastructure.
Smishing and Vishing
Detecting and disrupting smishing and vishing threats requires a multi-threaded detection and disruption methodology. Netcraft can detect and take down malicious phone numbers, as well as any links to additional attacker-controlled infrastructure used to support the attack.
Survey and Support Scams
Survey scams trick victims into thinking they’ll get a valuable reward, often using well-known brand names and fake gift card offers. Technical support scams involve fake agents — usually via calls or pop-ups — claiming there’s a problem with your device to steal personal info or charge for bogus help.
Malware
Instead of stealing information directly, this attack lures users to a site that secretly installs malicious code on their device. It can involve infected files, malicious documents, harmful JavaScript, or shopping site skimmers. Netcraft helps stop these threats by detecting and blocking malicious websites.
Ransomware
Respond to the first signs of a cyber attack by taking down the machines targeting your organization, whether they’re part of custom-built attack infrastructure or compromised devices in botnet attacks. Many organizations use SIEM tools to detect failed logins, blocked exploits, and mitigate denial of service attacks. Netcraft automatically uses this data to counter cybercriminals in real time, eliminating the need for manual intervention.
Web Shells
Malicious scripts known as web shells are implanted on compromised servers to give attackers remote control and unauthorized access. They serve as persistent backdoors for executing commands and manipulating the server. Netcraft identifies, blocks, and removes these web shells, cutting off attackers from restarting or escalating their campaigns.
Phishing
Netcraft takes down around one-third of the world’s phishing attacks, operating with careful automation on a global scale, establishing us as the most trusted takedown provider in the world.
Conversational Scams
Netcraft uses AI to engage directly with scammers, allowing us to detect and interact with received scams targeting your company to reveal the anatomy of the scam, exposing any financial details, and take down attack infrastructure.
Smishing and Vishing
Detecting and disrupting smishing and vishing threats requires a multi-threaded detection and disruption methodology. Netcraft can detect and take down malicious phone numbers, as well as any links to additional attacker-controlled infrastructure used to support the attack.
Survey and Support Scams
Survey scams trick victims into thinking they’ll get a valuable reward, often using well-known brand names and fake gift card offers. Technical support scams involve fake agents — usually via calls or pop-ups — claiming there’s a problem with your device to steal personal info or charge for bogus help.
Malware
Instead of stealing information directly, this attack lures users to a site that secretly installs malicious code on their device. It can involve infected files, malicious documents, harmful JavaScript, or shopping site skimmers. Netcraft helps stop these threats by detecting and blocking malicious websites.
Ransomware
Respond to the first signs of a cyber attack by taking down the machines targeting your organization, whether they’re part of custom-built attack infrastructure or compromised devices in botnet attacks. Many organizations use SIEM tools to detect failed logins, blocked exploits, and mitigate denial of service attacks. Netcraft automatically uses this data to counter cybercriminals in real time, eliminating the need for manual intervention.
Web Shells
Malicious scripts known as web shells are implanted on compromised servers to give attackers remote control and unauthorized access. They serve as persistent backdoors for executing commands and manipulating the server. Netcraft identifies, blocks, and removes these web shells, cutting off attackers from restarting or escalating their campaigns.




Unmatched Scale and Effectiveness

250+
Global Proxy Networks to evade criminal detection and cloaking techniques

85K+
Ever-growing proprietary rules as a detection force multiplier

23B+
Proprietary data points injected annually to deliver unmatched accuracy and visibility

100+
Different attack types detected across the largest data set in the industry

250+
Global Proxy Networks to evade criminal detection and cloaking techniques

250+
Global Proxy Networks to evade criminal detection and cloaking techniques

250+
Global Proxy Networks to evade criminal detection and cloaking techniques

85K+
Ever-growing proprietary rules as a detection force multiplier

23B+
Proprietary data points injected annually to deliver unmatched accuracy and visibility

100+
Different attack types detected across the largest data set in the industry
Frequently Asked Questions
What is Netcraft’s threat intelligence?
We process reports from our cybercrime detection platform, including our reporting community, industry and partner feeds, large-volume spam email datasets, and customers’ own reporting mechanisms — covering enterprises and governments, large and small — alongside our own discovery techniques. Suspicious URL feeds are typically very high volume and have a low signal-to-noise ratio: validation prior to blocking is essential.
A sophisticated automated classification system then confirms the attack type and attributes it to an impersonated entity. We handle a very wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis is heavily automated and operates without intervention around the clock, with manual involvement limited to edge cases, high-risk blocks, and for the purpose of improving future automated classification.
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are widely licensed by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is ongoing.
How do you validate threats?
Netcraft’s analysis is heavily automated and operates without intervention around the clock, with manual involvement only required for a tiny minority of edge cases, high-risk blocks, and for the purpose of improving future automated classification.
This includes:
A global network of fetch locations that are intelligently selected to defeat criminals’ attempts to restrict access using IP blocking
Rule-based matching across thousands of potential target organizations
Automatic classification based on previously seen phishing content
Machine learning based on previous classification by rule-based or human classification
Proactively interacting with forms using a headless web browser, submitting realistic data and exploring multi-stage attacks
How can my organization benefit?
As Netcraft’s threat intelligence feeds are truly global and cover impersonated organizations, whether they are customers or not, our feeds are used by browsers, antivirus companies, internet infrastructure providers, and impersonated enterprises themselves.
Threats impersonating your brand can be sent for disruption and takedown, and those which may affect staff members — like email and work collaboration platforms — can be used within your information security team in SIEM products and to block access within browsers with our apps and extensions.
How do you prevent false positives?
Netcraft operates both human and automated false positive fail-safes for high-risk potential blocks. Netcraft’s decades of experience exploring the internet allow us to rely on hosting provider data and other sources of intelligence on legitimate organizations’ own infrastructure. Where there is reason to be cautious, we require a second human verification before blocking.
Who else contributes to Netcraft’s threat intelligence?
Netcraft collates and validates reports from many of the world’s largest banks, threat intelligence providers, and anti-cybercrime organizations. Netcraft also recovers URLs from ongoing analysis of malicious email attachments, many of which serve as key infrastructure in malware operations.
What is Netcraft’s threat intelligence?
We process reports from our cybercrime detection platform, including our reporting community, industry and partner feeds, large-volume spam email datasets, and customers’ own reporting mechanisms — covering enterprises and governments, large and small — alongside our own discovery techniques. Suspicious URL feeds are typically very high volume and have a low signal-to-noise ratio: validation prior to blocking is essential.
A sophisticated automated classification system then confirms the attack type and attributes it to an impersonated entity. We handle a very wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis is heavily automated and operates without intervention around the clock, with manual involvement limited to edge cases, high-risk blocks, and for the purpose of improving future automated classification.
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are widely licensed by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is ongoing.
How do you validate threats?
Netcraft’s analysis is heavily automated and operates without intervention around the clock, with manual involvement only required for a tiny minority of edge cases, high-risk blocks, and for the purpose of improving future automated classification.
This includes:
A global network of fetch locations that are intelligently selected to defeat criminals’ attempts to restrict access using IP blocking
Rule-based matching across thousands of potential target organizations
Automatic classification based on previously seen phishing content
Machine learning based on previous classification by rule-based or human classification
Proactively interacting with forms using a headless web browser, submitting realistic data and exploring multi-stage attacks
How can my organization benefit?
As Netcraft’s threat intelligence feeds are truly global and cover impersonated organizations, whether they are customers or not, our feeds are used by browsers, antivirus companies, internet infrastructure providers, and impersonated enterprises themselves.
Threats impersonating your brand can be sent for disruption and takedown, and those which may affect staff members — like email and work collaboration platforms — can be used within your information security team in SIEM products and to block access within browsers with our apps and extensions.
How do you prevent false positives?
Netcraft operates both human and automated false positive fail-safes for high-risk potential blocks. Netcraft’s decades of experience exploring the internet allow us to rely on hosting provider data and other sources of intelligence on legitimate organizations’ own infrastructure. Where there is reason to be cautious, we require a second human verification before blocking.
Who else contributes to Netcraft’s threat intelligence?
Netcraft collates and validates reports from many of the world’s largest banks, threat intelligence providers, and anti-cybercrime organizations. Netcraft also recovers URLs from ongoing analysis of malicious email attachments, many of which serve as key infrastructure in malware operations.
What is Netcraft’s threat intelligence?
We process reports from our cybercrime detection platform, including our reporting community, industry and partner feeds, large-volume spam email datasets, and customers’ own reporting mechanisms — covering enterprises and governments, large and small — alongside our own discovery techniques. Suspicious URL feeds are typically very high volume and have a low signal-to-noise ratio: validation prior to blocking is essential.
A sophisticated automated classification system then confirms the attack type and attributes it to an impersonated entity. We handle a very wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis is heavily automated and operates without intervention around the clock, with manual involvement limited to edge cases, high-risk blocks, and for the purpose of improving future automated classification.
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are widely licensed by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is ongoing.
How do you validate threats?
Netcraft’s analysis is heavily automated and operates without intervention around the clock, with manual involvement only required for a tiny minority of edge cases, high-risk blocks, and for the purpose of improving future automated classification.
This includes:
A global network of fetch locations that are intelligently selected to defeat criminals’ attempts to restrict access using IP blocking
Rule-based matching across thousands of potential target organizations
Automatic classification based on previously seen phishing content
Machine learning based on previous classification by rule-based or human classification
Proactively interacting with forms using a headless web browser, submitting realistic data and exploring multi-stage attacks
How can my organization benefit?
As Netcraft’s threat intelligence feeds are truly global and cover impersonated organizations, whether they are customers or not, our feeds are used by browsers, antivirus companies, internet infrastructure providers, and impersonated enterprises themselves.
Threats impersonating your brand can be sent for disruption and takedown, and those which may affect staff members — like email and work collaboration platforms — can be used within your information security team in SIEM products and to block access within browsers with our apps and extensions.
How do you prevent false positives?
Netcraft operates both human and automated false positive fail-safes for high-risk potential blocks. Netcraft’s decades of experience exploring the internet allow us to rely on hosting provider data and other sources of intelligence on legitimate organizations’ own infrastructure. Where there is reason to be cautious, we require a second human verification before blocking.
Who else contributes to Netcraft’s threat intelligence?
Netcraft collates and validates reports from many of the world’s largest banks, threat intelligence providers, and anti-cybercrime organizations. Netcraft also recovers URLs from ongoing analysis of malicious email attachments, many of which serve as key infrastructure in malware operations.
What is Netcraft’s threat intelligence?
We process reports from our cybercrime detection platform, including our reporting community, industry and partner feeds, large-volume spam email datasets, and customers’ own reporting mechanisms — covering enterprises and governments, large and small — alongside our own discovery techniques. Suspicious URL feeds are typically very high volume and have a low signal-to-noise ratio: validation prior to blocking is essential.
A sophisticated automated classification system then confirms the attack type and attributes it to an impersonated entity. We handle a very wide range of cybercrime, including phishing, malware, and malicious JavaScript. Our analysis is heavily automated and operates without intervention around the clock, with manual involvement limited to edge cases, high-risk blocks, and for the purpose of improving future automated classification.
Once confirmed, threat data is included in our threat intelligence feeds, and our clients can begin the disruption and takedown process. Our threat intelligence feeds are widely licensed by browsers, antivirus companies, and internet infrastructure providers, protecting billions of people from cyber attacks while the takedown process is ongoing.
How do you validate threats?
Netcraft’s analysis is heavily automated and operates without intervention around the clock, with manual involvement only required for a tiny minority of edge cases, high-risk blocks, and for the purpose of improving future automated classification.
This includes:
A global network of fetch locations that are intelligently selected to defeat criminals’ attempts to restrict access using IP blocking
Rule-based matching across thousands of potential target organizations
Automatic classification based on previously seen phishing content
Machine learning based on previous classification by rule-based or human classification
Proactively interacting with forms using a headless web browser, submitting realistic data and exploring multi-stage attacks
How can my organization benefit?
As Netcraft’s threat intelligence feeds are truly global and cover impersonated organizations, whether they are customers or not, our feeds are used by browsers, antivirus companies, internet infrastructure providers, and impersonated enterprises themselves.
Threats impersonating your brand can be sent for disruption and takedown, and those which may affect staff members — like email and work collaboration platforms — can be used within your information security team in SIEM products and to block access within browsers with our apps and extensions.
How do you prevent false positives?
Netcraft operates both human and automated false positive fail-safes for high-risk potential blocks. Netcraft’s decades of experience exploring the internet allow us to rely on hosting provider data and other sources of intelligence on legitimate organizations’ own infrastructure. Where there is reason to be cautious, we require a second human verification before blocking.
Who else contributes to Netcraft’s threat intelligence?
Netcraft collates and validates reports from many of the world’s largest banks, threat intelligence providers, and anti-cybercrime organizations. Netcraft also recovers URLs from ongoing analysis of malicious email attachments, many of which serve as key infrastructure in malware operations.
Resources & Insights
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.
Book a Demo Today
Learn more about Netcraft’s powerful brand protection, external threat intelligence, and digital risk protection platform.



