
Disruption & Takedowns
Minimize the impact of cyber attacks by blocking and removing malicious content using Netcraft’s automated takedown platform

Detecting and disrupting cyber threats to mitigate risk
Once a cyber attack—a phishing website, fake social media profile, or fraudulent email, for example—has been detected through Netcraft’s cybercrime detection or by your own team and validated with our threat intelligence process, Netcraft blocks access to the attack and begins the takedown process.
Once blocked, users of the Netcraft apps and extensions are immediately protected. Netcraft also licenses its feeds to browsers and antivirus companies along with internet infrastructure companies, protecting billions of internet users from potential exposure while Netcraft’s automated takedown services work to rapidly take the attack offline completely.
Defeating cyber attacks with unmatched scale and effectiveness
Netcraft’s online brand protection operates 24/7 to discover phishing, fraud, scams, and cyber attacks through extensive automation, AI, machine learning, and human insight. Our disruption & takedown service ensures that malicious content is blocked and removed quickly and efficiently—typically within hours.

0%
of the world’s phishing attacks taken down

0M+
threat reports and suspicious URLs analyzed every day

0M
cybercrime attacks blocked to date

0M+
attacks taken down and growing
Rapid takedown of malicious content
Netcraft’s takedown service leverages extensive automation to:
- gather and present convincing evidence of the malicious content
- identify hosting providers, domain registrars, webmasters, social media platforms, and others involved in the attack’s infrastructure
- send notifications to each party using email, API, partner contact, and other escalation channels
- monitor attacks, during and after the takedown process to ensure it is truly eliminated
Essential to Netcraft’s success is our transparent evidence-driven approach combined with the respect and trust we have earned over decades of experience. This enables productive relationships to disrupt and takedown attacks swiftly.

Technology is only part of the story
Netcraft services are designed and built by our team of cybercrime experts, who have the agility and experience to adjust to new threats and attack types as they emerge.
While the platform’s automation is designed to operate at scale and around the clock, our technical operational teams can step in to help with escalated website and domain takedowns adding a human touch—including making phone calls and liaising with webmasters, hosting companies and social media platforms.
Common threat types
Netcraft’s digital risk protection platform covers 100+ cyber attack types including phishing, malware, advance fee fraud, and much more. Some of the following are the most prominent threats experienced by customers.

Phishing
Phishing attacks deceive individuals into revealing sensitive information, such as passwords or credit card details, by impersonating trustworthy entities through fraudulent websites, emails, or SMS messages.
Netcraft takes down around one-third of the world’s phishing attacks, operating with careful automation and global scale.
Conversational Scams
These rely on the interaction between the criminal and victim, through email, text message, or chat app. The scammer engages the victim in a conversation, often manipulating emotions or exploiting a sense of urgency, and eventually requests money.
Netcraft can detect and interact with received scams targeting your financial institution to reveal the anatomy of the scam, exposing any financial details and take down any additional attack infrastructure.
Vishing and Smishing
Cyber attacks conducted through a phone call or text message, where the criminal pretends to represent a trusted organization and encourage the victim to visit a link or to play along in a conversational scam.
Netcraft can detect and take down malicious phone numbers, as well as any links to additional attacker-controlled infrastructure used to support the attack.
Survey and Support Scams
Survey scams mislead victims into thinking they will receive a high-value reward or prize for providing their feedback. Often piggybacking on legitimate brands’ reputation, including branded gift cards.
Technical support scams involve criminals posing as technical support agents, usually through phone calls or pop-up messages, tricking victims into believing their devices are infected or have issues. The scammers aim to gain access to sensitive information or extort money for fake services.
Malware
Instead of tricking the victim into providing sensitive information, this type of attack lures users to a website where malicious code is unleashed and installed on the victim’s device.
This includes infected executable files, documents, websites infected with evil JavaScript and shopping site skimmers.
Ransomware
Respond to the first signs of a cyber attack by taking down the attackers’ machines targeting your organization. This includes anything from cyber criminal’s bespoke attack infrastructure to compromised devices used in botnet attacks.
Many organizations use SIEM (Security Information and Event Management) tools to identify failed login attempts, blocked exploits from web application firewalls, and mitigated denial of service attacks. Netcraft automatically leverages this data—so there’s no need for any manual interventions—to fight back against cybercriminals in real time.
Web Shells
These malicious scripts or programs that attackers implant on compromised web servers are used to gain remote control and unauthorized access. Web shells provide a persistent backdoor for hackers to execute commands and manipulate the server.
Netcraft finds, blocks, and takes down web shells that are associated with existing cyber attacks, denying the criminal further opportunities to restart existing attacks or launch new campaigns.
Frequently Asked Questions
Combining both takedowns and blocking in Netcraft’s threat intelligence feeds together allows cyber attacks to be mitigated most effectively. While Netcraft’s apps and extensions benefit from the full range of blocked attack types, not everybody has these installed and active. Collectively, Netcraft’s threat data partners—which includes browsers and antivirus companies—protect billions of people within minutes and this provides a second layer of protection. That protection is, however, at the discretion of each partner. Some may take longer than others to act and others may vary the protection level across desktop and mobile platforms.
By complementing blocking with takedowns, Netcraft ensures a proactive approach by promptly removing the malicious content at its source, regardless of the devices or systems in use.
Cybercriminals can make use of a variety of different hosting platforms, domain names, and other infrastructure to power their attacks, including:
- Webmasters: in the case of a compromised website, the webmaster may be entirely unaware of their own website being taken over by a criminal and will be able to respond decisively. In other cases where a lookalike domain has been used, the webmaster is the criminal and contacting them may be actively harmful.
- Domain registrars and registries: a domain name registrar handles the purchase and registration of domain names. You can find a website’s registrar information using a database like WHOIS or RDAP. Domain name registries, those that directly control a whole TLD like .fr, can also be involved in some circumstances.
- Hosting companies: a hosting company provides the platform and services required to keep a website online. Often, a hosting company can provide valuable data, logs, and information left behind by the criminal that can help identify impacted customers and mitigate damage caused by the attack.
- Social media platforms: for fake social media profiles, ads, and posts, there is often only a single party with influence over the attack—the social media platform itself.
- Email providers: Email providers can disable accounts used to disseminate fraudulent emails, including those that link to malicious content. It’s often necessary to have access to the full email, including its mail headers, which detail the origin of the email.
- Upstream providers: The upstream provider is an internet service provider (ISP) that provides bandwidth and facilitates the connection to a smaller network. In some circumstances, particularly where whole networks appear to be controlled by an attacker, upstream providers may be able to discontinue service.
- Law enforcement agencies: Depending on the type and impact of the attack, you may need to contact the law enforcement agency in the hosting company’s local jurisdiction.
Infrastructure providers need detailed evidence about the attack before they act. The more information provided, the better positioned we are to expedite the takedown. Evidence includes the:
- URLs and domain names involved in the attack
- IP address (or addresses)
- screenshots and videos of the attack
- known access restrictions. For example, an attack may only be visible on mobile networks in the targeted country. If not provided, the provider will not be able to confirm the attack and will not be able to act on the request.
Netcraft takes an evidence-based approach, leading to the respect and trust we have earned over decades of experience. This enables productive relationships to disrupt and takedown attacks swiftly.
We automatically identify hosting providers, domain registrars, social media platforms, webmasters and others, and determine how to notify them most effectively (via email, API, private contact, or otherwise). We then gather and present evidence of the cyberattack to demonstrate the problem to those with the ability to remove the attack.
Attacks are monitored for seven days after they are taken down, and if malicious content returns, the takedown process is restarted.
Netcraft can remove over 100 different attack types, including phishing, malware, fraudulent social media profiles, fake shops, and brand infringement.
Yes. Our web platforms and flexible APIs integrate with external threat intelligence and enterprise systems, making it simple to track and share critical incident data and events.
Insights
Blog
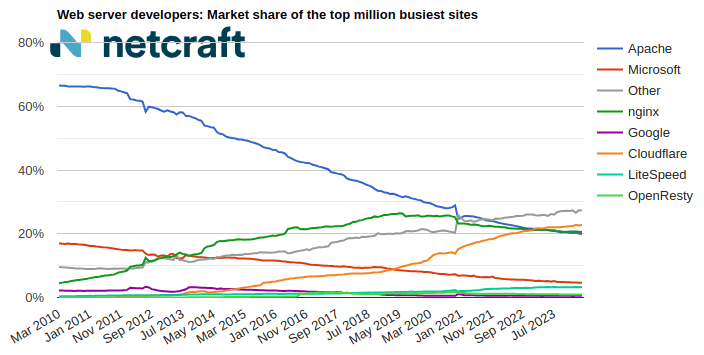
April 2024 Web Server Survey
In the April 2024 survey we received responses from 1,092,963,063 sites across 267,934,761 domains and 12,872,291 web-facing computers. This reflects … Read More
Learn More
Blog
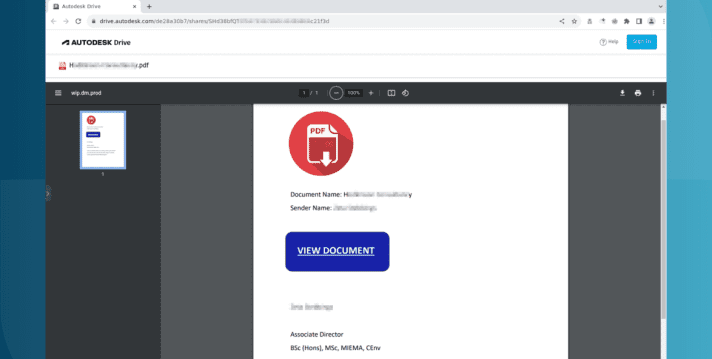
Autodesk hosting PDF files used in Microsoft phishing attacks
Autodesk is hosting malicious PDF files that lead phishing attack victims to have their Microsoft login credentials stolen. The elaborate … Read More
Learn More
Blog
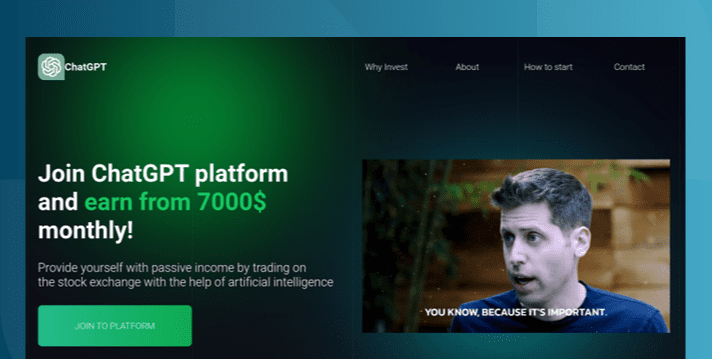
The AI Gold Rush: ChatGPT and OpenAI targeted in AI-themed investment scams
Investment scams and AI – a match made in heaven? Online investment scams are a big money spinner for … Read More
Learn More
Schedule time with us
Learn more about Netcraft’s powerful brand protection, external threat intelligence and digital risk protection platform