In just one month, certificate authorities have issued hundreds of SSL certificates for deceptive domain names used in phishing attacks. SSL certificates lend an additional air of authenticity to phishing sites, causing the victims’ browsers to display a padlock icon to indicate a secure connection. Despite industry requirements for increased vetting of high-risk requests, many fraudsters slip through the net, obtaining SSL certificates for domain names such as banskfamerica.com (issued by Comodo), ssl-paypai-inc.com (issued by Symantec), and paypwil.com (issued by GoDaddy).
CloudFlare, a content delivery network that provides free "Universal SSL" to its customers, is a hotspot for deceptive certificates, accounting for 40% of SSL certificates used by phishing attacks with deceptive domain names during August 2015. CloudFlare’s Universal SSL certificates are provided in partnership with Comodo, and CloudFlare also use GlobalSign certificates for some of its customers. CloudFlare’s flexible SSL option also appeals to fraudsters, offering a padlock in victims’ browsers without the need for attackers to set up SSL on their web servers.
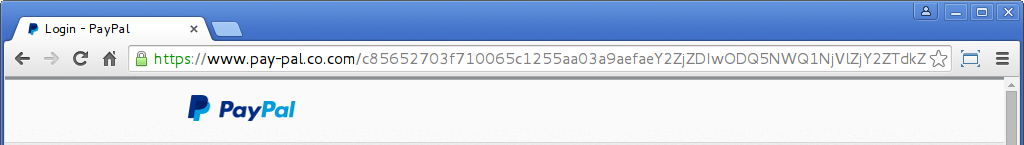 A screenshot of a PayPal phishing site using a widely trusted SSL certificate valid for www.pay-pal.co.com. The certificate is a CloudFlare Universal SSL certificate issued by Comodo. The certificate has not been revoked; however, the phishing site is no longer available.
A screenshot of a PayPal phishing site using a widely trusted SSL certificate valid for www.pay-pal.co.com. The certificate is a CloudFlare Universal SSL certificate issued by Comodo. The certificate has not been revoked; however, the phishing site is no longer available.
Websites that use TLS (the successor to SSL) are marketed as being trustworthy and operated by legitimate organisations. Consumers have been trained to “look for the padlock” in their browser before submitting sensitive information to websites, such as passwords and credit card numbers. While the reality is more nuanced, the data submitted to a phishing site using TLS is protected from eavesdroppers. However, a displayed padlock alone does not imply that a site using TLS can be trusted, or is operated by a legitimate organisation.
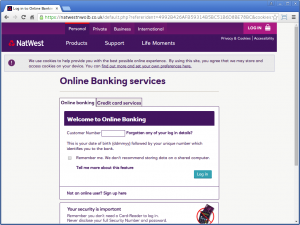 A screenshot of a NatWest phishing site using a widely trusted SSL certificate valid for natwestnwolb.co.uk. (nwolb stands for NatWest online banking. The legitimate NatWest online banking service is available at www.nwolb.com.)
A screenshot of a NatWest phishing site using a widely trusted SSL certificate valid for natwestnwolb.co.uk. (nwolb stands for NatWest online banking. The legitimate NatWest online banking service is available at www.nwolb.com.)
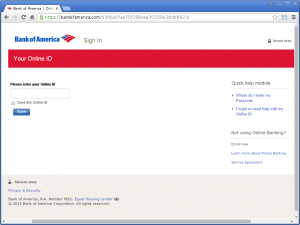 A screenshot of a Bank of America phishing site using a widely trusted SSL certificate valid for banskfamerica.com.
A screenshot of a Bank of America phishing site using a widely trusted SSL certificate valid for banskfamerica.com.
The following table lists some examples of deceptive SSL certificates that have been used to conduct phishing attacks, along with their Domain Registration Risk scores:
| Hostname | Phishing Target | Certificate Authority | Assurance | Risk Score | Revoked |
|---|---|---|---|---|---|
| halifaxonline-uk.com | Halifax | GlobalSign (CloudFlare) | OV* | 10.0 | No |
| emergencypaypal.net | PayPal | Comodo (CloudFlare) | OV* | 9.17 | Yes |
| blockchaín.info (xn--blockchan-n5a.info) | Blockchain | GlobalSign (CloudFlare) | OV* | 8.52 | No |
| blockachain.info | Blockchain | Comodo | DV | 8.42 | No |
| itunes-security.net | Apple iTunes | Symantec | DV | 8.08 | No |
| phypal.com | PayPal | Symantec | DV | 6.61 | No |
| btintranert.com | BT | GoDaddy | DV | 5.56 | Yes |
* The certificates that CloudFlare issues to its customers are ostensibly organisation-validated, as they contain CloudFlare’s company name and address. However, the customer domains themselves are only domain-validated.
The CA/Browser Forum’s Baseline Requirements – a set of rules that publicly-trusted certificate authorities are expected to follow – require that high-risk domain names that may be used for fraud or phishing are subjected to additional verification:
High Risk Certificate Request: A Request that the CA flags for additional scrutiny by reference to internal
criteria and databases maintained by the CA, which may include names at higher risk for phishing or other
fraudulent usage.
The CA SHALL develop, maintain, and implement documented procedures that identify and require additional
verification activity for High Risk Certificate Requests prior to the Certificate’s approval.
Despite this requirement, many major certificate authorities issue SSL certificates for deceptive domains used in phishing attacks. Notable exceptions include DigiCert and Entrust, neither of which issue domain-validated certificates.
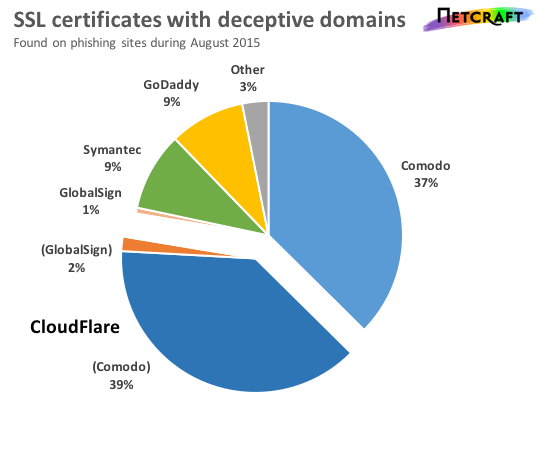
A pie chart showing SSL certificates containing a deceptive domain name that were used in phishing attacks during August 2015, split by certificate authority. CloudFlare and non-CloudFlare certificates are shown separately.
Certificate authorities commonly provide SSL certificates at three different levels of assurance:
-
Domain validated (DV)
Certificate authorities only have to check that the certificate’s applicant controls the domain name contained in a DV certificate. These certificates are typically the cheapest option, and can be had for free or be purchased for less than $10. Let’s Encrypt is planning to offer free, automatically-issued DV certificates starting later in 2015. -
Organisation validated (OV)
In addition to validating the domain name in the certificate, the identity of the person or organisation applying for an OV certificate is also verified by the certificate authority and included in the certificate. Most browsers do not treat OV certificates any differently to DV certificates. -
Extended validation (EV)
Like OV certificates, the identity of the organisation applying for an EV certificate is verified by the certificate authority. However, the verification is more stringent. EV certificates also receive different treatment in major web browsers – the address bar is either partially or completely coloured green and the requesting organisation’s name and country are displayed next to the padlock. The requirements for EV certificates in Chrome are changing, with many certificate authorities caught out by recent changes to require Certificate Transparency.
The requirement to perform additional verification of high risk certificate requests applies to all levels of assurance. However, DV certificates are often issued completely automatically within minutes, making it easy for fraudsters to obtain DV certificates for deceptive domain names.
Several certificate authorities offer free trial certificates with shorter validity periods. For example, Comodo offers free 90 day certificates, which have been used by a number of SSL phishing attacks. Symantec also offers free 30 day certificates through its GeoTrust brand. The short validity periods are ideal for fraudsters as phishing attacks themselves typically have short lifetimes.
Netcraft’s Domain Registration Risk service automatically identifies deceptive domain names constructed using such tricks. The service calculates a risk score between 0 (low risk) and 10 (high risk) for each domain name, which represents the likelihood that the domain name will be used to carry out a phishing attack. Certificate authorities can make use of the service to determine if a domain name is likely to be used for fraudulent purposes before issuing the certificate.
The service can be provided as an API that mimics a Certificate Transparency log server for ease of integration with your existing certificate issuance process. The same API can also be used with Netcraft’s certificate compliance checking service, which can identify certificates before they are issued that do not conform with the CA/B Forum’s Baseline Requirements or its EV Guidelines.