Some Content Delivery Networks (CDNs) enable fraudsters to deploy phishing attacks with valid SSL certificates. Not only does this make the fraudulent sites appear more credible, but they also benefit from the fast response times provided by the CDN.
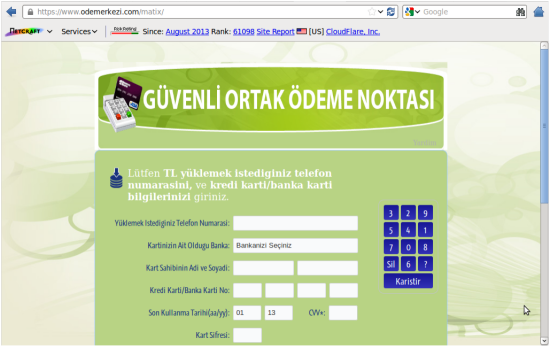
The phishing site on odemerkezi.com is targeted at Turkcell customers — visitors to the phishing site are asked for their phone number, bank name, credit card details, and password. As CloudFlare’s SSL feature is only available on paid accounts (which start at $20/month), the fraudster may have used an early victim’s credit card to purchase the Pro plan.
Netcraft is currently blocking hundreds of phishing attacks which use CloudFlare’s content delivery network, including some which use CloudFlare-provided SSL certificates. So far this year, Netcraft has blocked more than 2,000 phishing attacks using Cloudflare’s infrastructure, of which approaching 200 used SSL.
CloudFlare’s SSL certificates make use of the Subject Alternative Name (SAN) extension, which allows an edge node to use a single certificate for multiple domains. In the case of www.odemerkezi.com, the edge node presented a certificate which had a common name (CN) of “ssl2796.cloudflare.com”, but also included the odemerkezi.com domain along with the domains of many other CloudFlare customers.
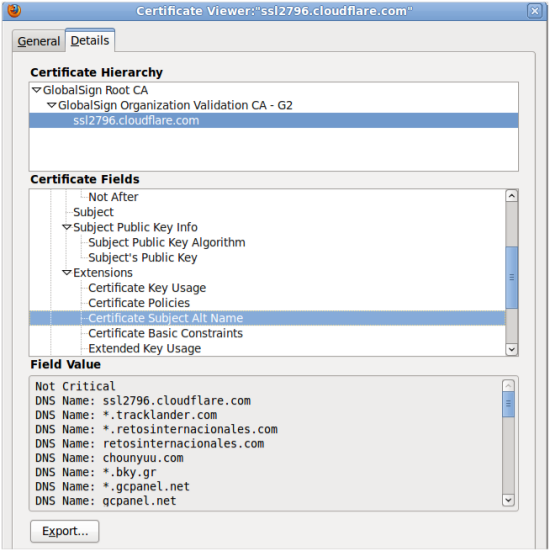
The multi-domain SSL certificates used by CloudFlare edge nodes are issued by GlobalSign. Rather than using Server Name Identification (SNI) — which would allow an individual certificate to be used for each website on a single IP address — CloudFlare uses GlobalSign’s Cloud product to work around a lack of support for SNI in Internet Explorer on Windows XP and some mobile browsers. The two companies announced their partnership less than a year ago, and GlobalSign’s own website uses CloudFlare, as do its OCSP and CRL services.
Some of the SSL phishing sites on CloudFlare that have been blocked by Netcraft have used deceptive domain names, such as paypal-germany.de.com, paypal-kundensicherheit.net and paypal-verifikation.com. Last month, a similarly deceptive domain name and SSL certificate issued by Network Solutions was used in a phishing attack against customers of Chase Bank.
Domain registrars and certificate authorities can reduce the likelihood of new domains and certificates being used for fraudulent activities. Netcraft’s Domain Registration Risk service identifies domains which are deceptively similar to legitimate websites run by banks and other institutions that are commonly targeted by phishing attackers.